The Security Policy of Sync Checker
When you launch Sync Checker for the first time, it will automatically integrate into the security model of macOS. This is necessary because the application can be used to perform critical operations in macOS, for example to alter or even delete operating system files. Only responsible system administrators who manage the respective computer should be allowed to perform such actions.
To guarantee a high security level, Sync Checker works in two parts: The normal main application with the graphical user interface is coordinating all operations. It also executes all tasks that don’t require any special permissions. However, as soon as a privileged operation has to be executed, for example reading a file owned by a different user, the application stops, makes you aware of the pending task, and checks whether the current user can identify herself as system administrator. If yes, the task will continue and the privileged operation can start.
The privileged job is not executed by the main application, however. A second component, the so-called privileged helper does this work by receiving the request of the main application via a secure, tap-proof channel. Even if an unauthorized attacker would manage to manipulate the main program, it could not trigger any malicious functions in the computer, because it could not get permission to do that. Only the privileged component, which is monitored and specially protected by macOS has this technical capability. This means we have a separation of user rights in this setup. The privileged helper will also be called security component in this context.
In case the current user cannot identify as system administrator, the privileged operation will be rejected, denying its execution. You receive a notice in the graphical user interface that the pending task could not be continued due to security reasons.
Approval to use the security component
Apple’s policies require an administrator to allow the security component to start automatically before Sync Checker can be used, since the security component provides services to all users. Such programs are referred to by Apple as Background Item.
The security component is started automatically by macOS when you start Sync Checker. It doesn’t run in the background when Sync Checker isn’t running.
Permission can be granted in two ways, either at the first launch of the program or at any time through the System Settings program. At the first start, the normal procedure is as follows:
- Start Sync Checker for the first time. The program does not open its control window, but instead displays an assistant guiding you through all necessary steps for the security component to be approved.
- macOS displays a request via the Notification Center at the top right, asking whether you like to allow a new background item. In this dialog, select Options > Allow.
- Confirm with an administrator’s password that you allow this for all users.
- Sync Checker removes its message window and starts its full user interface.
You can also grant permission at any time through the System Settings program. Perform the following steps:
For macOS 15 Sequoia:
- Quit Sync Checker if it is running.
- Launch System Settings.
- Open General > Login Items.
- Find Sync Checker in the Allow in the Background list.
- Make sure the switch for this entry is on.
For macOS 26 Tahoe:
- Quit Sync Checker if it is running.
- Launch System Settings.
- Open General > Login Items & Extensions.
- Find Sync Checker in the list App Background Activity.
- Make sure the switch for this entry is on.
Confirming a privileged operation
To create the aforementioned monitored link between main application and privileged component, macOS asks for permission to setup the helper program during the first start of Sync Checker. After this special trust relationship has been established between main application and privileged component, Sync Checker will begin to control the special permissions from there on. The following rules apply when verifying the right to execute a protected operation:
For security reasons, only those users can initiate a privileged operation in Sync Checker for which the option Allow user to administer this computer is enabled in the account management of macOS. Such users are called administrators. This special option is the default for the user who owns the computer and has set it up.
The application cannot read your password: Neither the main application, nor its privileged component are involved in the password entry and verification of credentials. Both tasks are exclusively handled by macOS, so that your password cannot be seen by the programs. Only after macOS has checked your identity, the result will be sent to the application.
The previous rule applies to the authorization of privileged operations, but not for other logins which can also be protected by passwords. If the application has to login to a server process or to another computer in the network, it can be necessary that the program has to temporarily accept the password itself for technical reasons. In such a case you will receive an explicit notification about this circumstance before.
On computers with Touch ID, the confirmation can also be done by fingerprint: If your computer contains Apple’s fingerprint reader Touch ID, the verification of your identity can also be done by fingerprint. As usual in macOS, you can choose whether to identify by password or by fingerprint.
A confirmation is valid for the pending operation, and optionally for further operations in the next five (5) minutes: In some cases, Sync Checker has to execute multiple privileged operations in rapid succession to achieve a certain process, for example, a protected file may need to be deleted, and another one must be created in a protected folder. The application is designed to handle such a composite operation as single event, even if the operations are internally considered separate actions requiring different permissions. You only have to authenticate once, not twice in this example. But even operations which don’t belong together don’t necessarily lead to a renewed password entry: If a time of less than five minutes has passed between a privileged operation and your last authorization, another check of your identity will be avoided.
An authorization won’t be shared with other applications: When you have confirmed your identity to Sync Checker to execute a privileged operation, this authorization will only be valid for the application itself, but not for other programs. This is also stricter than the usual guidelines of macOS, which would permit to avoid another password entry within five minutes for all applications running in the same login session.
Current limitations of macOS
Sync Checker adheres strictly to Apple’s current guidelines for providing privileged security components. Unfortunately, the latest technologies that Apple prescribes for their implementation are not always mature. This can depend on the macOS version you are using. In particular, the following restrictions may apply at the moment:
There should only be one copy of the program on your computer. You should avoid having multiple versions or multiple copies on your Mac when launching the program. Only backup copies on Time Machine volumes are accepted.
While you start the Mac, macOS must be able to “see” the application on the startup volume. So it should be in the folder Applications on the startup volume or a subfolder of it.
Additional limitations may exist in specific versions of macOS. You may also find detailed information in the chapter Important Release Notes.
Removing outdated generations of the security component
Sync Checker has a long history, protecting many generations of the operating system with its security architecture. Because Apple has changed the guidelines and technologies for this aspect of the system many times, it can have been necessary in the past to modify the security component to use a completely new technology. Usually you won’t need to care about this. The application will notify you when an update is due and will perform all necessary steps by itself.
There can be cases however, where an updated security component is so different from its predecessor versions that it will no longer be compatible with them and cannot remove them automatically due to technical reasons. This means an outdated copy of the privileged helper could still be present in the system, even if the main application has been deleted or updated in the meanwhile. This usually doesn’t bother, because macOS only starts these programs when necessary. You may like to delete these old components however, to avoid possible misuse and to clean up your computer.
Sync Checker offers a special maintenance feature to do this. It can search for outdated auxiliary programs and remove them if desired. Perform the following steps:
- Launch Sync Checker if it is not running yet.
- Select the menu item Tools > Clean Old Security Components….
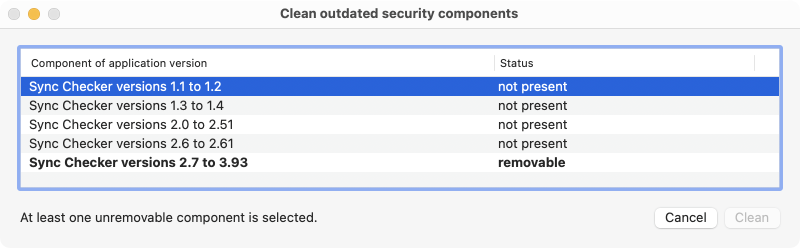
A window like that depicted in the example will open. The table lists all components which could still be installed from old versions of the application. Components marked by bold print are indeed still present and appear with the status removable. You can select one or more of these components and click the button Clean to delete them. If components are still in use unexpectedly, this will be automatically detected. You can only remove such helper programs after quitting their associated main applications.
Enabling stricter policies for administrator authorization
In older versions of the application, there were special cases for authorizing privileged operations where a login of a user with administrative rights was not allowed for security reasons. If desired, administrators can reinstate this previous, more restricted behavior.
Authorization in the current login session of a user who does not have administrative privileges
A user who is not currently logged in to macOS as an administrator can still perform privileged operations if they know the administrator credentials. The current login session does not need to be interrupted. If this option is not desired for security reasons, an administrator can block this by entering the following command on the affected computer:
sudo defaults write /Library/Preferences/com.bresink.system.syncchecker.plist MBSBlockAuthForNonAdminLogin -bool true
Fallback from local user identification to administrator authorization with name and password
To recognize users as authorized for a privileged operation, the application uses a feature of macOS known as local user authentication. macOS checks the user’s identity through a dialog window that asks for their credentials. Alternatively, it is also possible to use security hardware, e.g. reading a fingerprint via Touch ID or using a smart card.
There are special cases where macOS rejects local user authentication, considering the user as unauthorized:
- The administrator has a blank password and this is not generally prohibited in the running operating system.
- Multiple users are currently logged into screen sessions on macOS and the administrator is accessing either via the feature Fast User Switching or through a network connection via screen sharing, but he does not currently have the “front” screen session (on the physical screen), so it is unclear who currently has access to Touch ID or other security hardware. This is called a non-interactive situation in macOS.
- Special hardware is available for user identification, but a technical problem has occurred.
In such cases, the program automatically switches to the traditional login of an administrator using name and password. If this option is not desired for security reasons, an administrator can block this by entering the following command on the affected computer:
sudo defaults write /Library/Preferences/com.bresink.system.syncchecker.plist MBSBlockLocalAuthFallback -bool true
Additional notes on changing security policies
Both policies mentioned above can be turned on or off independently. As a rule, the change takes effect the next time you start the application. However, there may be special operating situations in which macOS delays activation. If you want to ensure that the change takes effect in any case, it is recommended to restart the computer.
The return key may only be pressed at the end of the command, even if a command may be shown on several lines for reasons of space. After command entry, macOS will ask for the password of the currently logged-in administrator. It is entered covertly, so it does not appear on screen.
To switch the behavior back to default, the following commands can be used:
sudo defaults delete /Library/Preferences/com.bresink.system.syncchecker.plist MBSBlockAuthForNonAdminLogin
or respectively
sudo defaults delete /Library/Preferences/com.bresink.system.syncchecker.plist MBSBlockLocalAuthFallback